I made a presentation the other day to a group of local business owners, it went really well so in response to that, here is the same information slightly condensed so everyone can benefit.
The topic today is “What is an SSD and how can it help me?”
You may have heard people talking about this but haven’t really given it much thought as to how you can take advantage of this rather new and exciting technology. What is an SSD and what does it do? How can it help me?
SSD is an acronym for Solid State Drive. It is a storage device that is required by a computer to store data, like the operating system (ie Windows), programs, documents, pictures, that sort of thing. I’ll also explain SSDs in another way, I’m sure everyone is familiar with the humble USB memory sticks, am I right? SSDs in a broad sense are very similar to a USB memory stick, but are far more sophisticated. They have no moving parts and information is stored in microchips.
The main benefit SSDs have over other forms of storage is speed. If you compare them to the traditional hard drive (or HDD), a HDD uses a mechanical arm with a read/write head to access the information from wherever it’s located on a storage platter. It’s the time it takes for the HDD to find this data that makes them much slower in comparison; it simply requires more physical labour (mechanical movement) to retrieve the information.
A typical SSD uses NAND-based flash memory, which is a non-volatile type of memory. What does non-volatile mean, I hear you ask? The simple answer is that whenever the drive looses power it won’t ‘forget’ what’s stored on it. This is essential otherwise the computer would have to be permanently powered on forever, not really practical is it? As a comparison, the RAM or system memory your computer uses is a form of volatile memory, whatever is stored in RAM is lost when power is interrupted. In this case, it’s perfectly acceptable and is by design.
SSDs have come a long way since they were first pioneered, they are able to be read and written to all day long and the data storage integrity will be maintained for many many years.
An SSD relies on an embedded controller processor for the drive to function. The controller is a very important factor in determining the speed of the SSD. There are a number of controller choices that manufacturers could use in their drives and having the right controller is often what separates an excellent SSD from a good one.
Sounds exciting right? I won’t go too much into the working of the traditional HDD, I’m sure we are all familiar; after all, they have been around for nearly sixty years. Yes, you read correctly; IBM introduced the first HDD back in 1956! We’re talking about sixty year old technology, although to give some credit, the technology has been refined over the years.
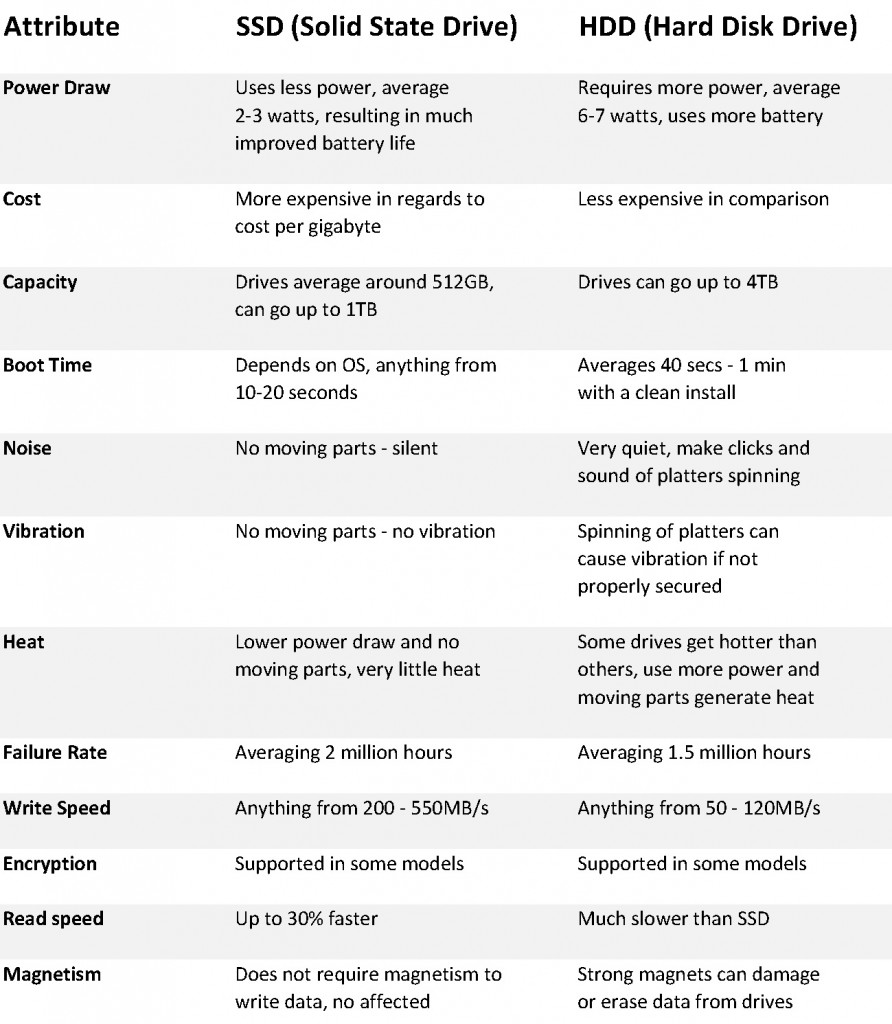
The pros & cons of each are listed in the table below.
As you can see, there are many benefits of an SSD over a HDD but it doesn’t automatically make them a better option. SSDs a still a relatively new form of storage and have a little while to catch up. Right now however, HDDs have the upper hand by offering more storage space for less cost. You may still be asking yourself, which drive is right for me?
- You are prepared to pay more for better performance
- Not concerned with having limited storage capacity or can work around it
- You need lots of storage capacity, up to 4TB for a single drive
- You don’t want to spend much money
- Not concerned about performance
HDDs are still a popular choice, most average consumers typically choose a HDD as the storage option in their new computer mainly due to cost. However, as SSD prices continue to fall, more and more consumers are considering these drives as an upgrade, this is a great way to get a more life out of an old laptop that may be a few years old. As they say, a computer is only as fast as its slowest component and for many years, the HDD has always been the bottleneck. At CKP Computers, we specialise in the highest quality components, computer repairs & service, so let us help you by installing a new SSD in your existing laptop. It will unleash a new lease of life to a slow and otherwise unproductive laptop, make your battery last longer and you can also possibly avoid the high cost of purchasing a new laptop prematurely.
When it comes to desktop computers, the ideal situation is to have both; an SSD which has the operating system and software applications installed on it in addition to a large multi GB HDD which is used purely for data storage (documents, photos, etc). Of course this is only possible in systems that have the provision of housing multiple storage devices.
If you would like more information on SSDs, please contact us today on 0447 619 397 or send us an enquiry, either through our contact page, by Facebook or by email, helpme@ckpcomputers.com.au.